Encryption Collection
"Unlocking the Secrets: Exploring the Fascinating World of Encryption" The Enigma code machine, a symbol of secrecy and intrigue during World War 2
All Professionally Made to Order for Quick Shipping
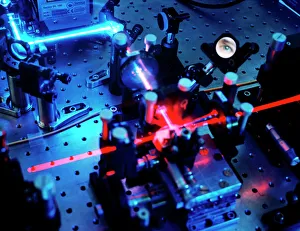
"Unlocking the Secrets: Exploring the Fascinating World of Encryption" The Enigma code machine, a symbol of secrecy and intrigue during World War 2. Delving into history: The Enigma encryption machine used by Allied forces to crack codes and turn the tides of war. Quantum cryptography equipment: Harnessing the power of quantum mechanics to secure our digital communications. U. S. Troops learn cryptography in Tarawa, Papua New Guinea, June 1943 - a sepia photo capturing their dedication to protecting sensitive information. An eye adorned with binary numbers, representing the ever-growing importance of digitalization and data protection. Unlocking mysteries: An illustration showcasing a cipher disc, an ancient tool for encrypting messages throughout history. F008 / 3263 - A secure website that ensures your online interactions remain private and protected from prying eyes. Conceptual artwork depicting internet security (F006 / 8838) - highlighting the crucial role encryption plays in safeguarding our online activities. Conceptual artwork illustrating network security (F006 / 8837) - emphasizing how encryption shields us from cyber threats lurking in the virtual realm. Protect yourself. Conceptual artwork portraying an unprotected network (F006 / 8731), reminding us to fortify our digital connections with robust encryption measures. Data security matters. A conceptual artwork (F006 / 9850) underlining how encryption safeguards valuable information against unauthorized access. In this rapidly evolving digital age, understanding encryption is paramount as it guards our secrets, secures our communication channels, and protects invaluable data from falling into wrong hands.